1. Run your win xp on virtual box
2. Make fuzzer like as Buffer overflow before this, but for this case we make fuzzer on comand "USV"
3. run Bigant server.
next open Ollydbg and attach Antserver.exe , next run ollydbg..
4. run your fuzzer..
#python dab.py
look register on ollydbg, there register EIP doesn't affected by buffer,
but EIP haved affected by buffer, for look that check on view -> SEH chain next type
Shift+F9
5. now we search address of jump (POP POP RETN)
for next step select view -> executable modules
for this case we select vbajet3.dll
next copy file vbajet32.dll to backtrack...
after copy, go to console
fot this case, i save vbajet32.dll on Worked
#./msfpescan -i /media/Worked/vbajet32.dll | grep SEHandler
#./msfpescan -i /media/Worked/vbajet32.dll |
# grep DllCharacteristics
6. next we search locate of POP, POP RETN
on ollydbg select view->executable modules->vbajet32.dll..after on CPU type right search for->sequence of comands
next input
POP r32
POP r32
RETN
on window
now ollydbg find address memory of vbajet32.dll
7. next search offset of overwrite SEH
we used pattern create and pattern offset
# ./pattern_create.rb 2500 > data.txt
next copy data to fuzzer
restart bigant and ollydbg again
next run fuzzer ..
after run fuzzer look the register haved change,next look on SEH chain and by pass that with click Shift+F9
now we have the value of register EIP for calculate byte of pattern_create result.. used pattern_ofset for do it..
#./pattern_offset.rb 42326742
966
next edit fuzzer
8. after edit fuzzer, restart again ollydbg and bigant...
run fuzzer..
now ollydbg show if bigant server is crash and happend access violaton on memory
..
look SEH chain...
9. make braekpoint on address of SEH..
next edit fuzzer ( add address of SEH )
now restart again bigant server and ollydbg..next run fuzzer...
view->SEH chain
table of SEH chain show to vbajet32.dll
click SHift+F9
proccess sent to stack..
this just have 4 byte, so we want search big space memory
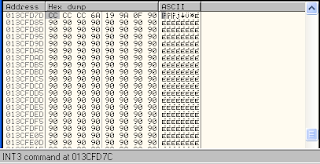
click right on 013CFD7C -> follow in dump->Selection
here have empty space begin of address 013CFD85
10. on assembly language, jump short have opcode \xEB\xZZ, ZZ is byte for added to jump...(e.g. \xEB\x02 this is jump 2 byte)
on this case we want jump 6 byte..before we edit fuzzer, first we make payload..
like as, run msfweb
#cd /pentest/exploits/framework2/
#./msfweb
open your browser and type 127.0.0.1:55555
select payload->os:win32->windows bind shell
click generate payload
copy shellcode to fuzzer
dont forget to breakpoint on address of SEH
next restart again bigant and ollydbg..after that run,next run fuzzer and look SEH chain
here look SHE chain have wrong saved, should file vbajet32.dll
now delete payload and run again fuzzer
here if payload haved delete and run fuzzer,, SEH chain show file vbajet32.dll...this mean happen on fuzzer and that is bad character....
11.Now we search where is bad character..we used perl language
open console and type
#perl generatecodes.pl 00,0a,0d
now input script to fuzzer line by line begin first line
remember, dont forget to breakpoint address of SEH before run fuzzer..
on first line, SEH chain go to right address that is vbajet32.dll, here we can say first line no bad character..
next input second line to fuzzer
restart bigant and ollydbg then run fuzzer,but remember you must always to breakpoint the address of SEH
after add second line to fuzzer, here out of SEH chain is 90909090, that mean is have bad character...
now we'll try to divide to 2 parts..
first, we input half of second line..
"\x12\x13\x14\x15\x16\x17\x18\x19
now run fuzzer again...
after run fuzzer, SEH chain show vbajet32.dll..
for two parts,,we'll to divide again
\x1a\x1b\x1c\x1d\ and x1e\x1f\x20"
now we input first buffer to fuzzer (\x1a\x1b\x1c\x1d)
run fuzzer again..
after fuzzer runing, SEH chain stay show vbajet32.dll
that mean is SEH chain show the right address
now we input second part to fuzzer, but here we just input \x1e and \x1f then left \x20
run fuzzer again..
wow, SEH chain stay show vbajet32.dll
that mean is \x20 bad character..
why ? because on ASCII \x20 is space character..
now we used generatecodes.pl for search bad character other with add \x20 to shellcode
go to console and type
#perl generatecodes.pl 00,0a,0d,20
now input shellcode to fuzzer
now restart bigant and ollydbg then run fuzzer..
SEH chain show vbajet32.dll
this is no bad character,,,but to ensure we'll do to compare between data on buffer appplication and data on shellcode..
12. now we check bad character on buffer
restart bigant and ollydbg then breakpoint to address of SEH 0F9A196A next run fuzzer...
now SEH chain show to address vbajet32.dll click Shift+f9
now click F7 three times for jump to past POP, POP RETN
now click F7 for bring you to 16 byte NOP..
look first character of shellcode transsmitted by fuzzer is \x01\x02
13. now we read buffer on memory with method dump body memory begin from address 012CF094
after follow in dump->selection
now look memory bottom left
now select data 01 till FF
click right binary->binary copy..
now paste data to text editor and save with name memory.txt
next save shellcode to file with name shellcode.txt
#perl generatecodes.pl 00,0a,0d,20 > shellcode.txt
14. compare file shellcode and memory used comparememory.pl
#perl comparememory.pl memory.txt shellcode.txt
now we look character \x25\x26\x27 lost and change with \x57.
that mean is one character of \x25\x26\x27 is bad character...
for know that, can use generate shellcode and lost one by one of three character then send shellcode to application..begin from \x25
#perl geeratecodes.pl 00,0a,0d,20,25
now send data to applicaton with fuzzer..
save data on buffer and compare with shellcode...
here show no compare with before and after sent.
so,we can conclusion if bad character is \x25...
now we have 5 bad chracter there is \x00\x0a\x0d\x20\x25
15. next step is make payload
click generate payload
next copy shellcode to fuzzer and run without ollydbg
final step
#telnet 192.168.56.101 4444
Thanks god !